Incident Reseponse & Forensic
January 27, 2026
Introduction
Introduction
Security incident definition
Definitions
A security incident refers to any unauthorized or unexpected event that poses a threat to the confidentiality, integrity, or availability of an information system or its data. It involves a violation of security policies or practices by an adversary with the intention to negatively affect an organization. Examples of security incidents include data breaches, ransomware attacks, and denial of service attacks.
Incident response is a cyber security function that uses various methodologies, tools and techniques to detect and manage security incidents and thus adversarial attacks, while minimising impact, recovery time and total operating costs.
Event is an observed occurrence within a system or network. It ranges from a user connecting to a file server, a user sending emails, or anti-malware software blocking an infection.
Incident is a violation of security policies or practices by an adversary to negatively affect the organisation through actions such as exfiltrating data, encrypting through ransomware, or causing a denial of services
We can find this concept in differents methods related the risk management (SSI):
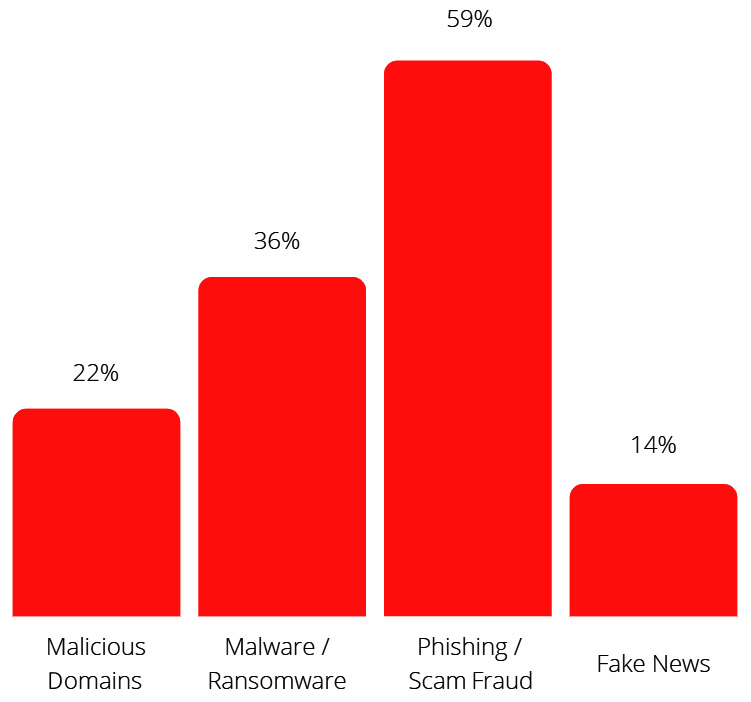
Threat Landscape and Cybersecurity incidents
Supply chain attacks
- They have been increasing in recent years –> organizations have not considered these attacks within their threat modeling
- Usually, third-party services or tools are considered part of the company’s ecosystem and are reliable, having a high trust level
- ShadowHammer (ASUS live utility)
- SolarWinds tool (used by red team of FireEye company)
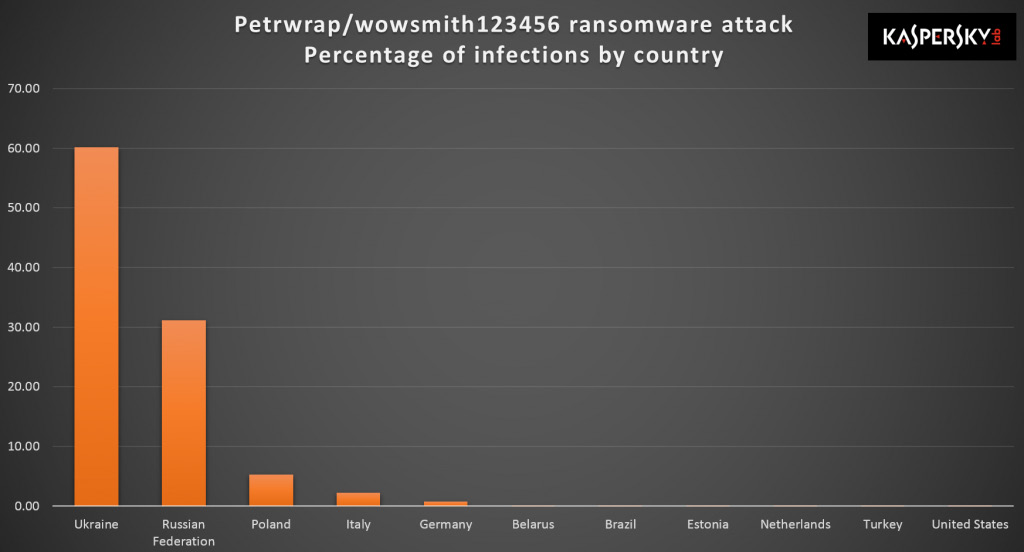
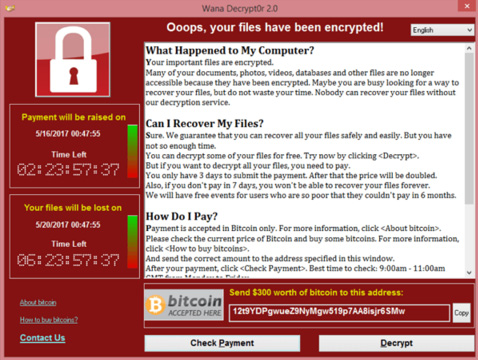
The ransomware
- Wanacry (exploited EternalBlue vulnerability - CVE-2017-0144,)
- Petya (None Financial objective)
Cyber attacks targeting IOT devices
- Mirai Botnet
- DDoS attacks on Dyn’s servers
Others
- Autonomous vehicles
- Electronic voting machines
- Drones & Cyber attacks on robots
Articles of law
- Related to offenses against automated data processing systems : Articles 323-1 à 323-8 du code pénal.
Complaint
- https://www.ssi.gouv.fr/en-cas-dincident/
- OCLCTIC, C3N, BEFTI , DGSI.
Types of security incidents
- Sabotage –> Integrity and Availability
- DoS –> Availability
- Spying –> confidentiality and integrity
- Ransomware –> Impacts availability, integrity and possibly confidentiality
- Others : Website defacement, Cryptocurrency mining, Database corruption, Identity theft.
Building an Incident Response Capability
- Security incidents can disrupt business operations, lead to information leaks and can impact the company’s image.
- Quick and appropriate response is crucial.
- Taking a proactive approach to incident response
- Having a plan, defined procedures and sufficient resources (infrastructure and tools) is essential.
- Frameworks and Preparation:
- Frameworks like NIST and SANS
Incident response standards and frameworks - NIST Handling Guide
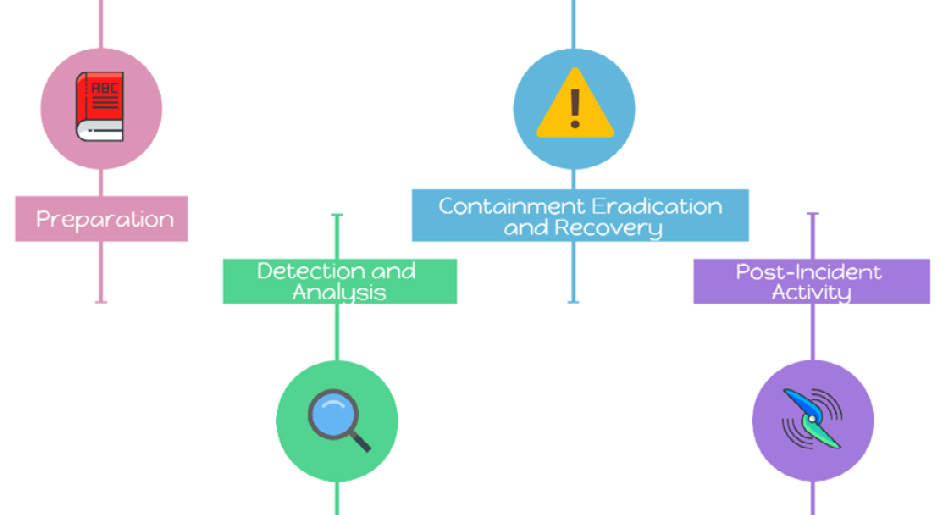
Incident response standards and frameworks - SANS handbook
Benefits
A reduction in the costs and the impact associated with the interruption of business operations of the company
Faster identification of the nature of the attack, discovery :
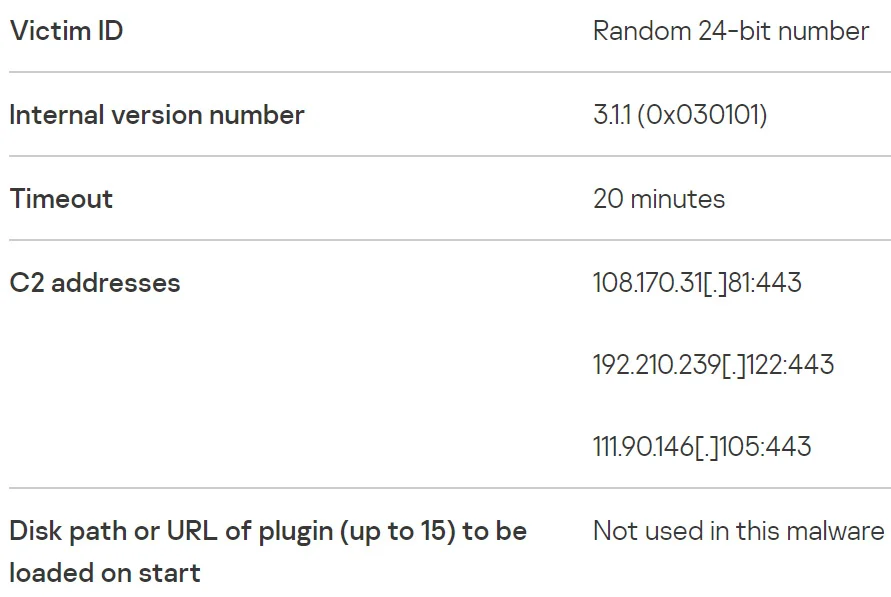
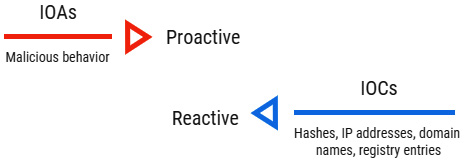
Indicators of Compromise (IoC)
Indicators of Attack (IoA)
improvement the organization’s ability to protect against future threats
IoC - IoA - Artifacts
Indicators of Compromise (IoC)
IoC is the detailed information stored in the forensic artifact and, from the forensics point of view, could be used to identify the presence of malicious activity.
Indicators of Attack (IoA)
The goal is to identify the attacker’s potential intentions, regardless of the tool they used

Developing organizational incident response capabilities
- Involvement of different areas of the organization.
- The technologies necessary to perform the triage and investigations.
- Operational resilience to guarantee business continuity and enable recovery from a disaster.
- Risk management and compliance that considers legal and regulatory aspects.
- The remediation of incidents must be related to business processes.
Creating IRP
IRP
An IRP is a document that describes the procedures to follow in case of a security incident. The IRP generally defines a route to follow when a security incident occurs. This plan must be consistent with existing organizational capacity, resources, and infrastructure.
The elements of an IRP
- Mission
- Objectives and strategies
- Management approval
- The organization’s position on IR
- Metrics to measure the capacity and efficiency of the plan
- Path to raise the maturity levels of the organization’s IR capability
- Definition of alignment of the plan with the organization
Different roles and responsibilities are defined, as follows
- Security operations center (SOC): This is the first line of defense, whereby staff are responsible for threat detection and triggering security alerts.
- Incident manager: Responsible for coordinating activities between stakeholders and determining the best plan of action.
- Computer IR team: They are responsible for following procedures and providing technical expertise.
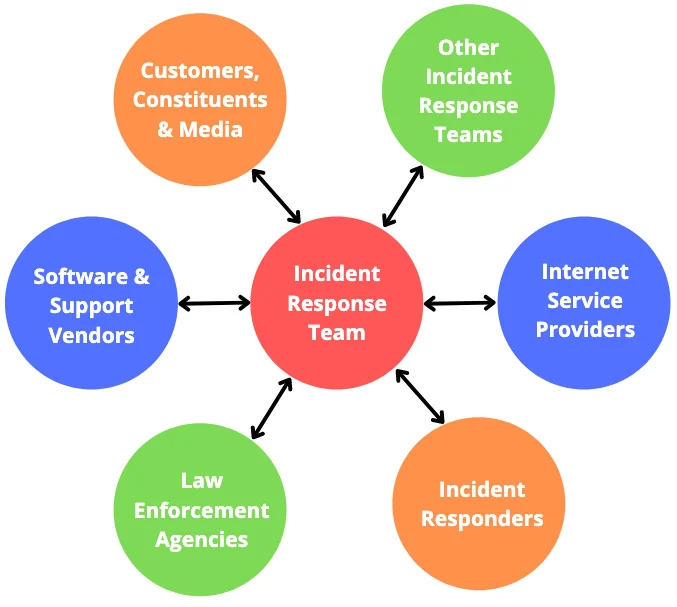
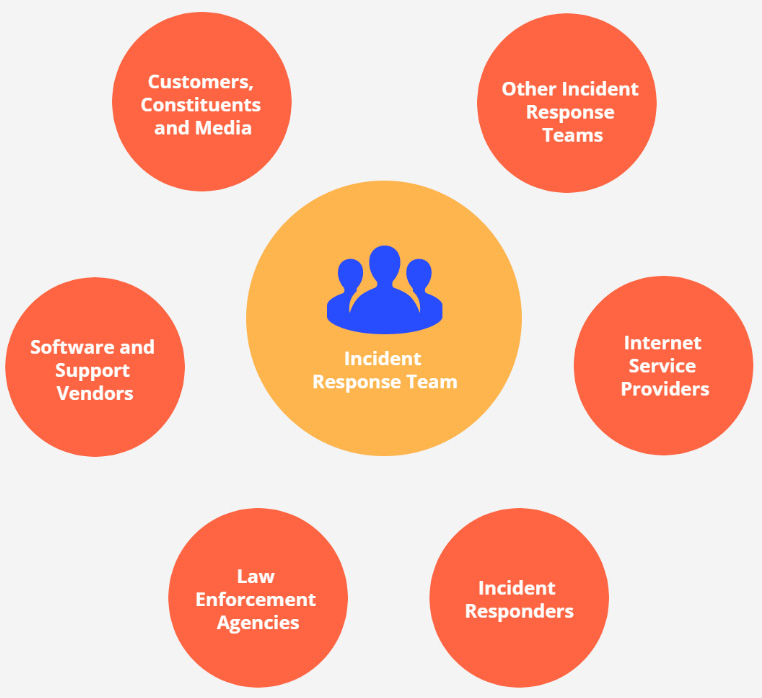
Who does incident response?
- CERT : Computer Emergency Response Team
- CSIRT : Computer Security Incident Response Team
- They can be public or private
CERT-FR
Provides 24/7 incident management support to:
Public sector (ministries, institutions, independent authorities, hospitals, local authorities…)
CERT-FR
It’s also:
A vulnerability watch service.
- Vulnerability researchers protected by article L. 2321-4.
The preferred international point of contact for all cyber incidentsincidents affecting France. This is achieved through participation in communities.
CERT-FR
They communicate trouh thier web site and X @CERT_FR:
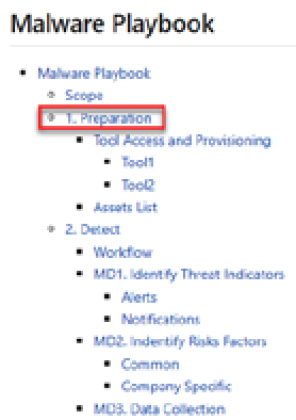
IR playbooks
IR playbooks
IR playbooks are detailed action plans that describe actions to be taken in specific security incidents. Unlike IRPs, these playbooks are more of the checklist type of actions for specific types of attacks such as phishing, information leaks, ransomware, denial-of-service (DoS) attacks, defacement of a website, and so on.
The components of an IR playbook could comprise the following
- The condition that initiates an incident
- Workflow of steps to follow
- The incident completion status
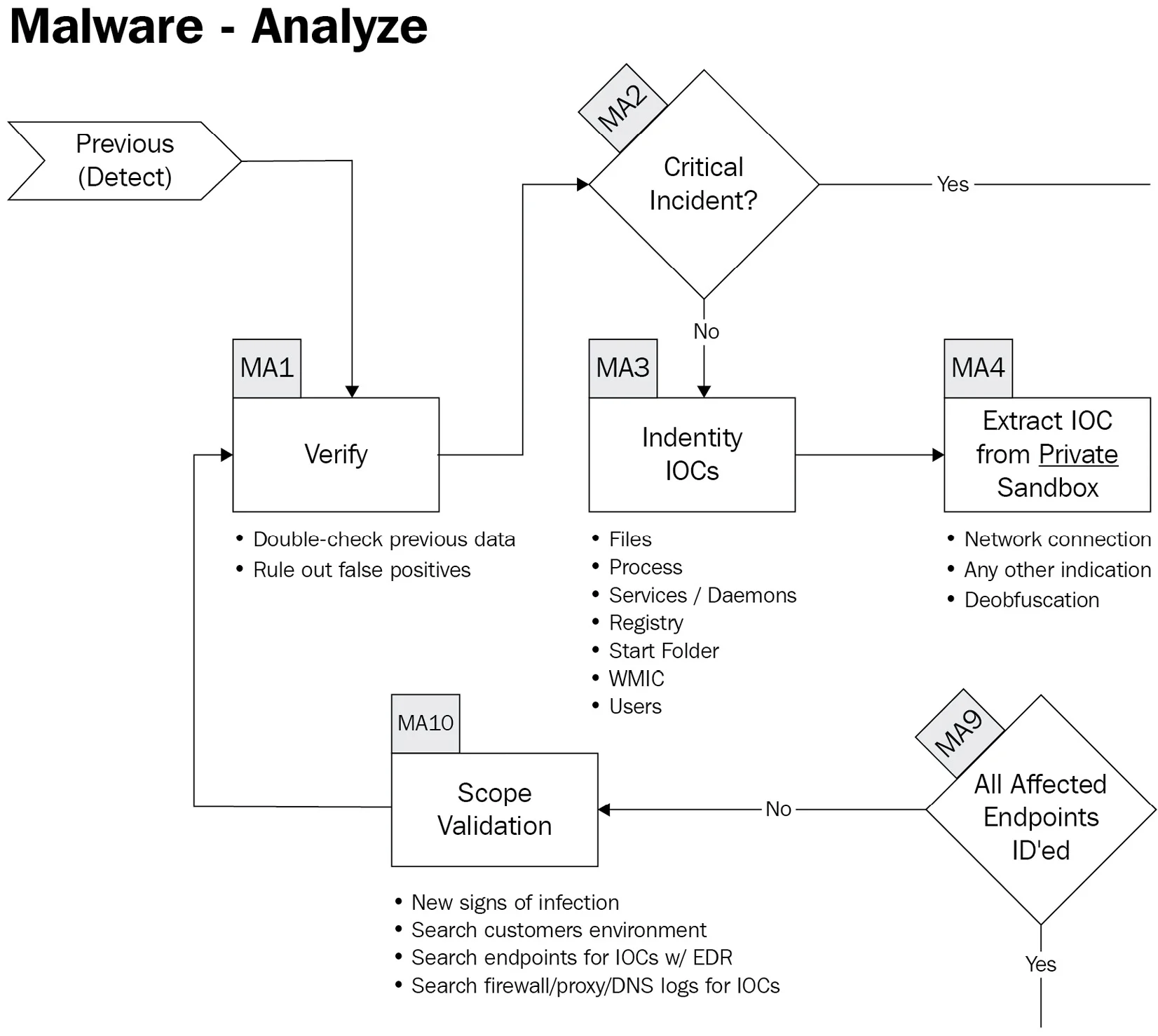
Incident Playbook
- aligned with the MITRE ATT&CK framework, and the playbooks are classified by tactics.
- Phishing example
- you can find specific tasks to be performed in the different stages of IR (investigate, remediate, contain, eradicate).
- The integration with Atomic Red Team for attack emulation is considered within its roadmap to test the playbooks.
Public Playbook
Testing IRPs and playbooks
- Once you have created an IRP and playbooks for different scenarios, it is advisable to carry out periodic evaluations
- It is recommended to use NIST Special Publication 800-84 Guide to Test, Training, and Exercise Programs for IT Plans and Capabilities to create a formal testing plan.
- The results of these tests should lead to improved quality and effectiveness of the plans
Simulation of attacks to measure response programs
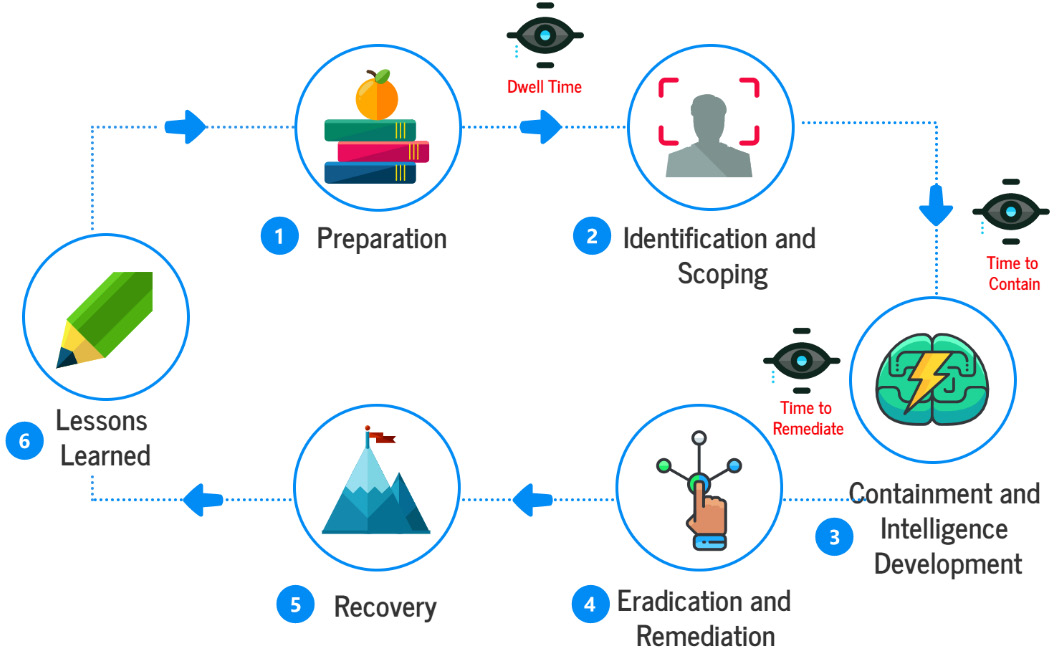
Digital Forensic
Responding to an incident within 72 hours of a security breach is essential for making decisions and taking actions to
identifyandcollectuseful information to assist inthreat containment.- it is crucial to coordinate incident response and digital forensic investigation activities.
Tradeoff between the urgency of returning to business operations and collecting the evidence necessary for the investigation and align business continuity goals with incident response plans.
Identification and Scoping
Event Notification
The loop begins when an issue has been reported. It triggers the incident response process and sets the stage for the subsequent steps.
Documentation
The underlying issue is documented in detail, including information about the nature of the incident, the systems affected, and any potential threats or vulnerabilities. Documentation is a critical step that provides a foundation for the rest of the process.
Evidence Collection
Evidence of the incident is collected, including log files, network traffic data, and other relevant information. The collected evidence provides valuable insights into the incident and helps identify potential threats.
Artefact Identification
The collected evidence is analysed to identify artefacts related to the incident. These artefacts can provide clues about the threat’s nature and the damage’s extent.
Pivot Point Discovery
Based on the identified artefacts, new areas of investigation may be discovered. These pivot points can lead to new insights and help further refine the incident’s scope. After this step, the process loops back to the documentation phase, incorporating the new findings.
First response guidelines
- Evaluating the context and the scene
- Securing the scene
- Identifying the sources of the evidence
- Establishing the legal admissibility of the evidence
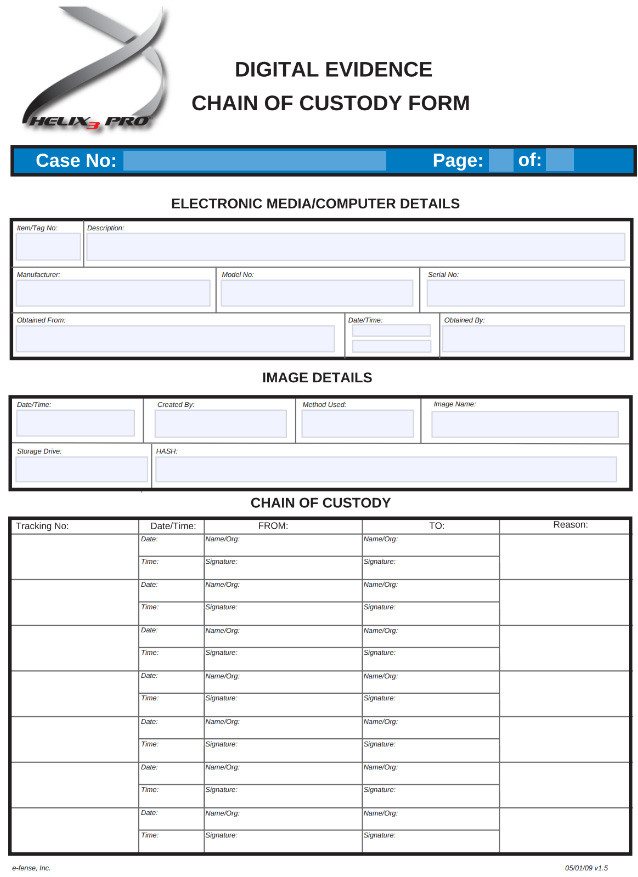
- Chain of custody
- Triage
- First response toolkit (TP)
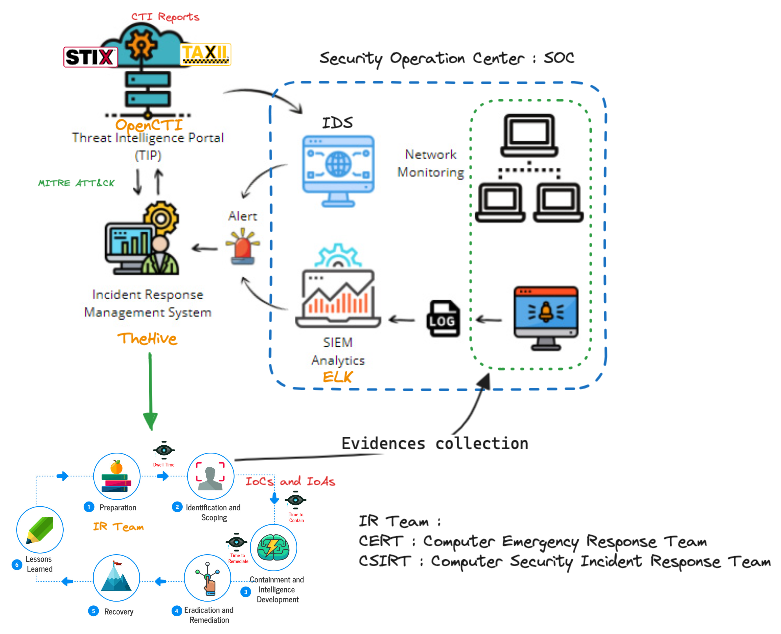
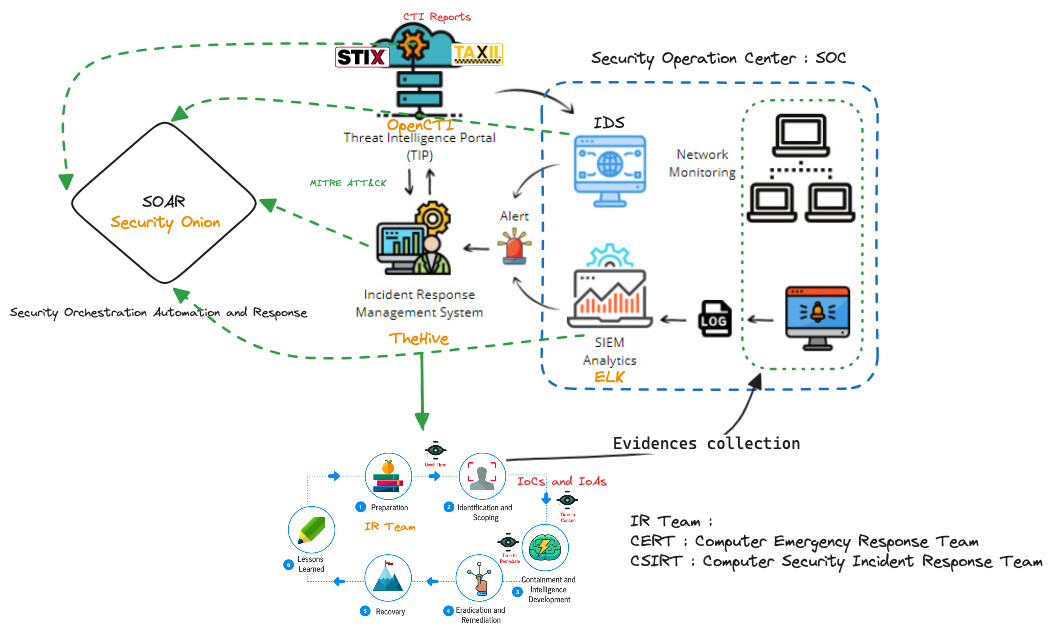
Using Cyber Threat Intelligence in Incident Response
CTI
Cyber Threat Intelligence (CTI) is crucial when responding to security incidents. The knowledge you have about threat actors and malicious campaigns gives you a strategic advantage to identify Indicators of Attack (IoAs) or Indicators of Compromise (IoCs) associated with a security breach faster and more efficiently.